Basic Concepts
From Jedisaber Wiki
CIA Triad
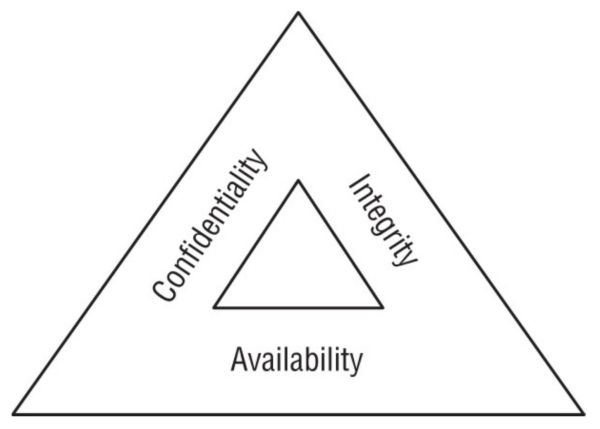
The three key objectives (CIA Triad) of cybersecurity programs are confidentiality, integrity, and availability.
- Confidentiality: Unauthorized users don't gain access. (Firewalls, ACL's, encryption)
- Integrity: No unauthorized modifications. (Hashing, monitoring)
- Availability: The system is up when users need it. (fault tolerance, clustering, backups)
Nonrepudiation: Someone who performed an action can't deny performing said action (Digital Signatures) (Not a part of CIA, but also important.)
DAD Triad
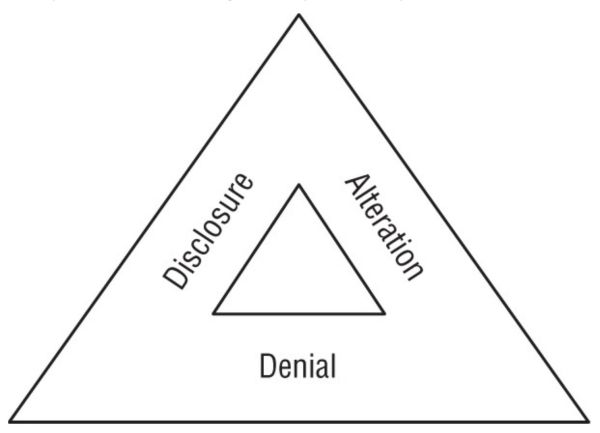
The the three key threats to cybersecurity efforts: disclosure, alteration, and denial.
- Disclosure: exposure of sensitive information to unauthorized individuals; violation of the principle of confidentiality (Attacks on the system, misconfigured credentials, lost devices)
- Alteration: unauthorized modification of information; violation of the principle of integrity (fraudulent transactions, typos, bit flip due to power loss)
- Denial: disruption of an authorized user's legitimate access to information; violation of the principle of availability (DDoS, failure of a server)
